Describe Best Practices for Using a Firewall
Dont use plagiarized sources. Try to use the same rule set for similar firewall policies with the same group object.
Network Segmentation Best Practices To Improve Security Web Filtering
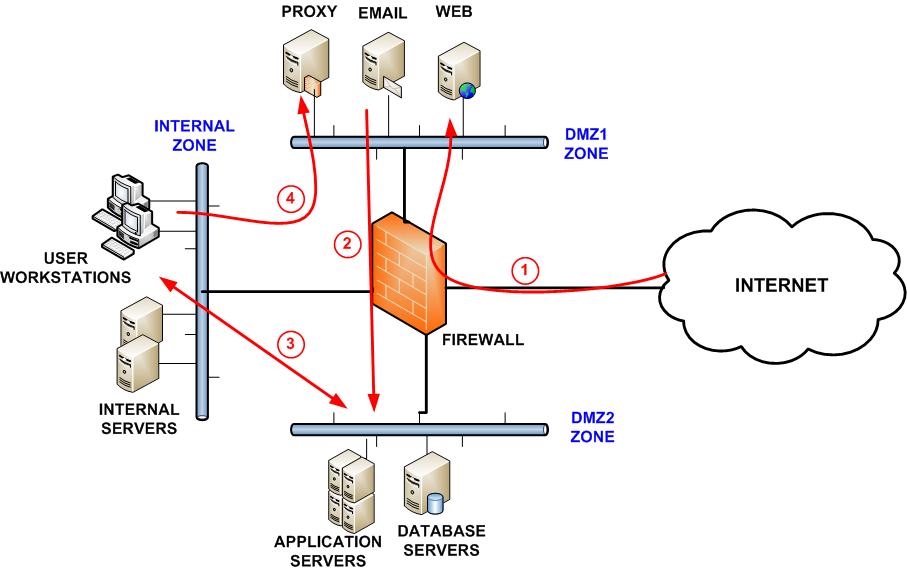
Traffic from the Internet is allowed by the firewall to DMZ1.
. List three of them. Use a 32-bit subnet mask when creating a single host address for example 255255255255. This may result in allowing every protocol through.
Dont complicate firewall management by unnecessarily nesting rule objects. Multi-vendor firewalls are operational in many. Disable services or software that arent needed and limit the applications that run on the firewall.
Reinforce an individuals right to use or sell encryption algorithms without concern. Block Traffic by Default. These recommendations cover a wide range of deployments including home networks and enterprise desktopserver systems.
Strengthen your firewall rules. The purpose of this chapter is to describe the best practices for performing such migrations and ultimately to ease the migration process itself. The following are some of the best practices applied to ensure proper firewall effectiveness and service.
But more importantly it lets you audit your firewalls architecture and streamline it if needed. Start blocking all traffic by default and only allow specific traffic to identified services. Managed firewalls and firewall-as-a-service offer a cloud-based rather than a device-based solution.
All other TCPUDP ports should be closed. With advancements in technology many processes have become faster and easier. The settings for a firewall policy should be as specific as possible.
Firewall management Firewall management can be the procedure of properly configuring and monitoring a firewall to maintain secure networks. Add expiry dates as comments for temporary rules and regularly review these dates for rule clean-up. Do not use 0000 as an address.
All traffic from the trusted network is allowed out. Publicly accessible servers should be authoritative-only. In many cases a next step for administrators will be to customize.
Get Your Custom Essay on Describe the Firewall management Just from 9Page Order Essay It is. In AWS firewall-as-a-service offers immediate protection and in some ways may be more cost-effective for smaller companies that may not be able to purchase and maintain the firewall infrastructure. Any DNS server should be part of a high-availability HA pair.
When you open the Windows Defender Firewall for the first time you can see the default settings. Traffic from the Internet to the servers in DMZ2 is not permitted at least not directly. Best practices for configuring Windows Defender Firewall Keep default settings.
Use subnets or specific IP addresses for source and destination addresses and use individual services or service groups. Entry-level to midrange hardware firewalls will have a throughput of roughly 500Mbps. Types of Best Practices Establish a Formal Change Procedure.
Migration Network administrators are often reluctant to change firewall vendors due to the perception that the migration process is difficult. Not only that the existing rule set needs to be constantly optimized for speed and performance based on this carefully framed firewall rule base security best practices. A firewall throughput applies to hardware firewalls and usually offers a range of firewall throughputs to choose from.
Firewall rules will need to be updated for any new services and new devices that. Set Explicit Firewall Rules First. Top 7 Best Practices for Using a Firewall Protection in 2021 1.
State that the use of encryption is not probable cause to suspect criminal activity. Best practices themselves are the result of user experiences in a given area and are not intended to be a one-size-fits-all description for appropriate firewall deployments. Periodically spring-clean your firewalls policies to maximize its performance and eliminate conflicting rules.
If your firewall comes with all ports and services open the easiest way to begin the rule-set setting procedure is to close them all and then open up only the services that you need. To open Windows Firewall go to the Start menu select Run type WFmsc and then select OK. Automation of firewall updates.
Do not use Any as a service. The firewall device is never accessible directly from the public network. Centralized management tool for multi-vendor firewalls.
Question 12 There are six recommended best practices for firewall use according to Laura Taylor. Avoid using the Any option in the firewalls Allow rules. As the number of network users goes up you will need a firewall to handle the demand.
Automatic port blocking is a term used to describe how some firewalls such as Symantecs VelociRaptor firewall come with their ports closed by default. The firewall should only permit traffic via certain ports 80443 25 etc. Configuring your Windows Firewall based on the following best practices can help you optimize protection for devices in your network.
Understand rule precedence for inbound rules. They should not act recursively. The process of adding deleting or modifying firewall rules should be well planned out Best practices firewall rules so that the performance of the existing rule set isnt negatively impacted.
Those individuals should be using the nameservers provided for use by their internet service provider ISP. Prohibit the federal government from requiring the use of encryption for contracts grants and other official documents and correspondence. Individuals outside your organization do not need to use your recursive nameservers.
Sql Server Patching Best Practices For 2022 Tek Tools
Applied Sciences Free Full Text Firewall Best Practices For Securing Smart Healthcare Environment A Review Html

A Cybersecurity Roadmap Cyberattacks Firewall Hackers Ransomware Infosec Datasec Cybe Cyber Security Technology Cyber Security Education Cyber Security

Enforce Your Aws Network Firewall Protections At Scale With Aws Firewall Manager Aws Security Blog
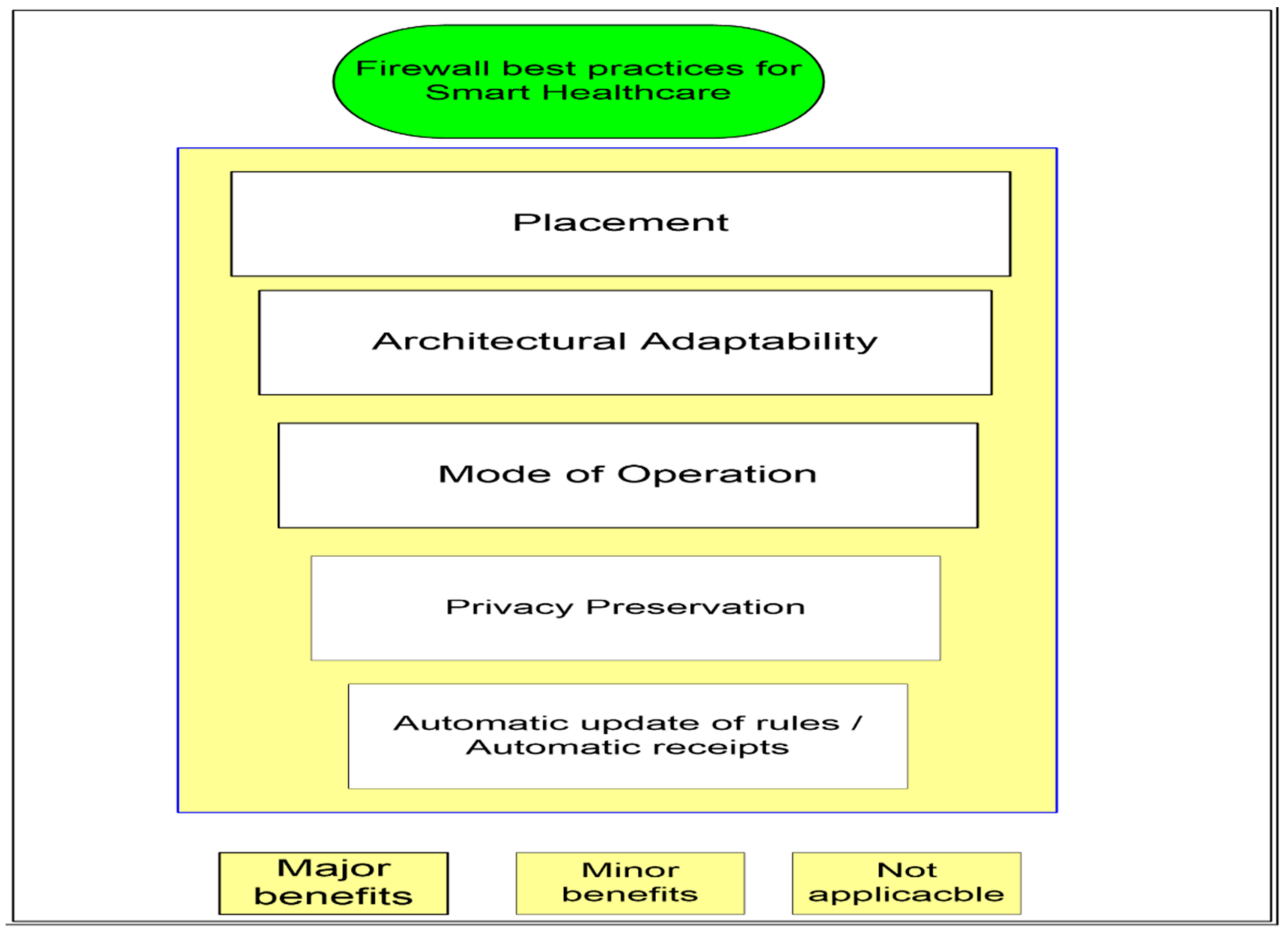
Applied Sciences Free Full Text Firewall Best Practices For Securing Smart Healthcare Environment A Review Html

Best Practices And Recommendations For Firewall Rules

Best Practices For Configuring Windows Defender Firewall Windows Security Microsoft Docs
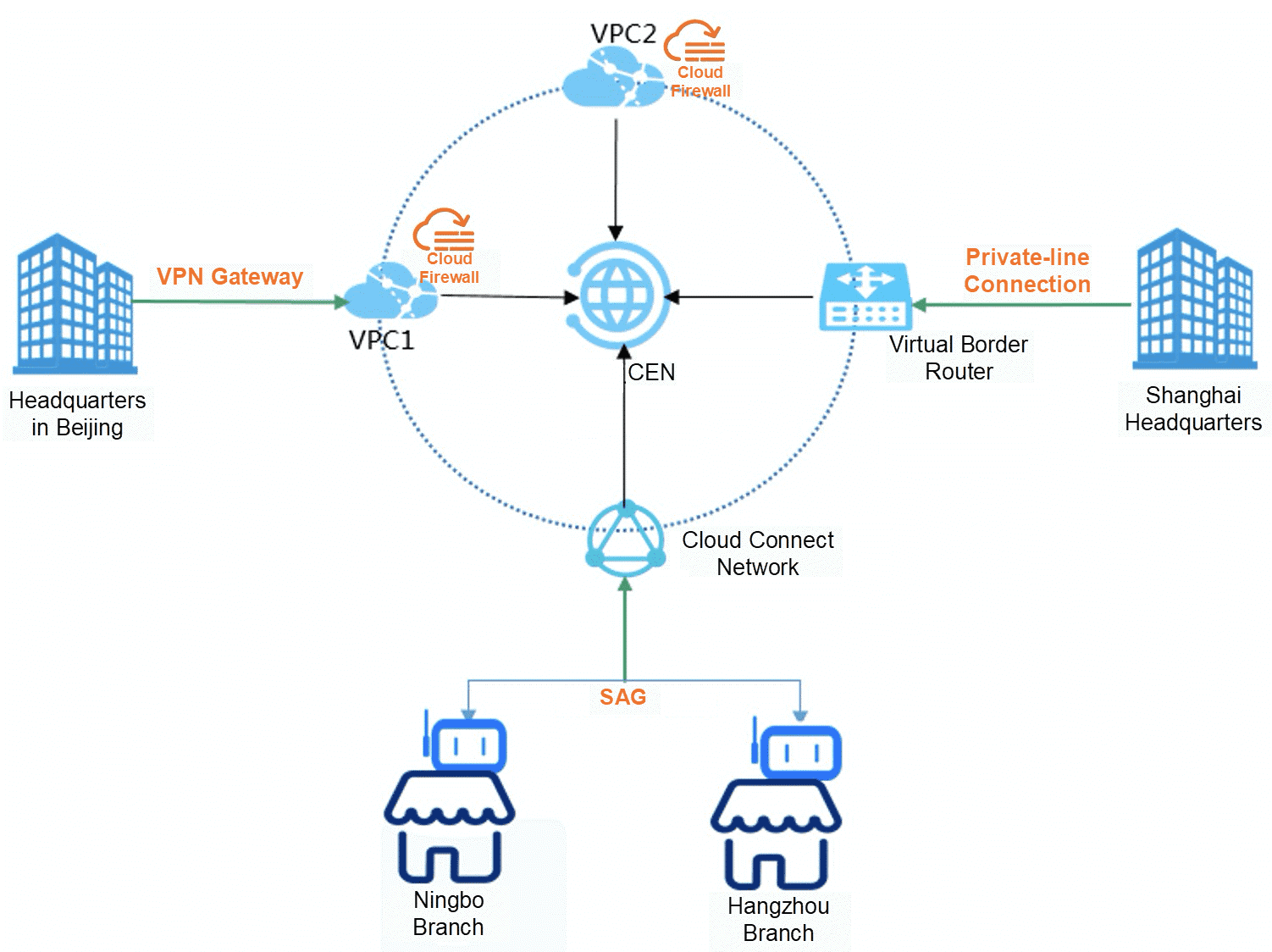
Best Practices For Building Secure Global Networks Internal And External Alibaba Cloud Community

Best Practices Pre R80 X Rulebase Construction And Optimization

Best Practice Assessment Bpa Overview Youtube
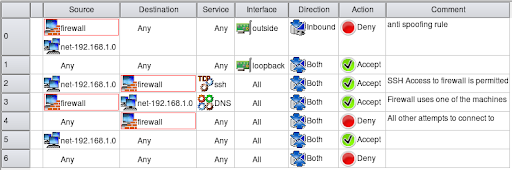
Best Practices For Configuring Firewall Rules Blumira
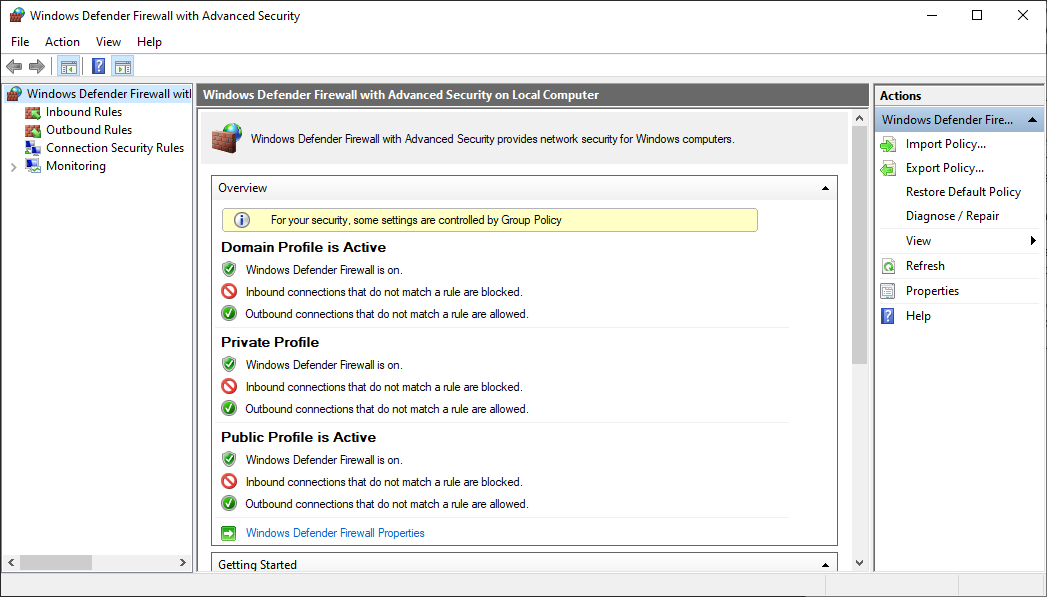
Best Practices For Configuring Windows Defender Firewall Windows Security Microsoft Docs
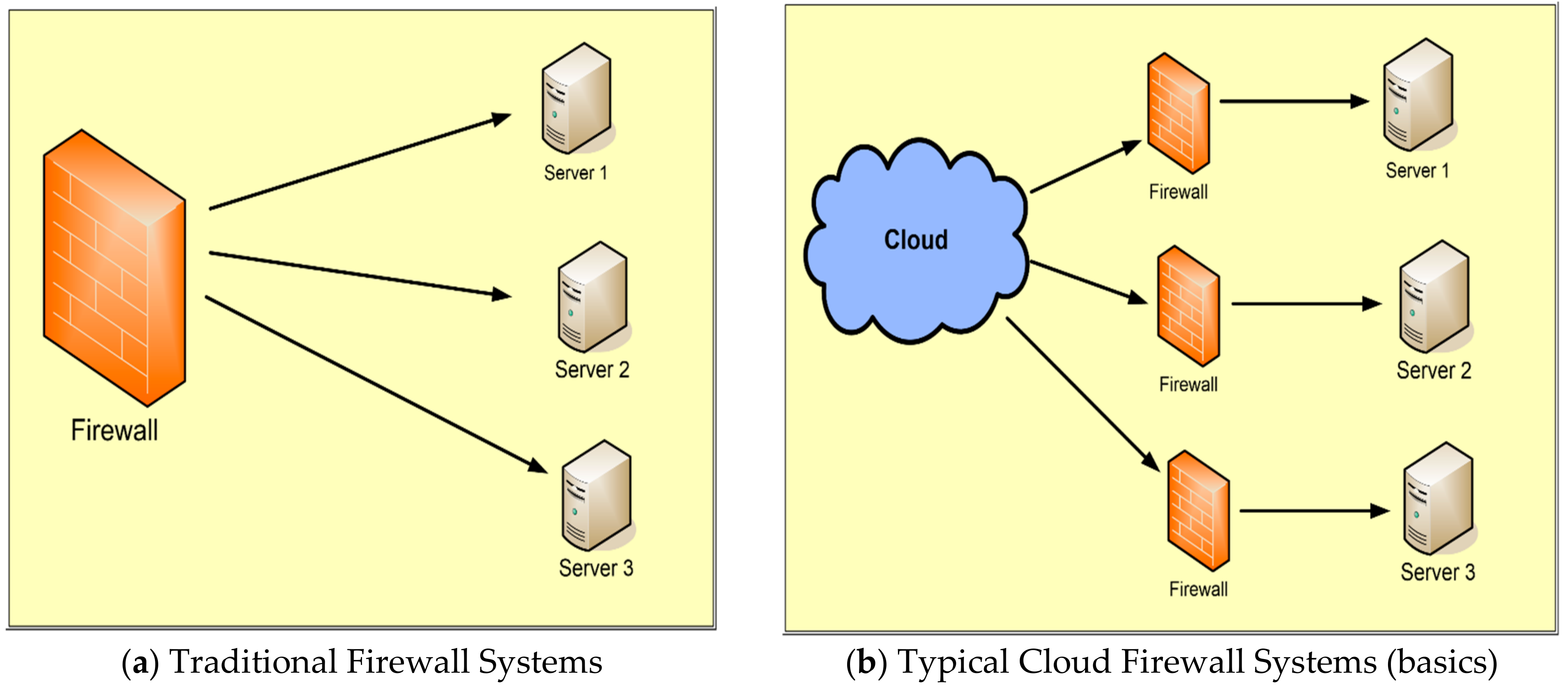
Applied Sciences Free Full Text Firewall Best Practices For Securing Smart Healthcare Environment A Review Html

Security Log Best Practices For Logging And Management Dnsstuff
Data Center Capacity Planning Best Practices Dnsstuff

Firewall Rule Base Cleanup Policy Examples Best Practices Tufin



Comments
Post a Comment